Vulnerability Disclosure Policy
Michelin (MFPM - Manufacture Française des Pneumatiques Michelin) has a CERT (Computer Emergency Response Team), that among its responsibilities is tasked with ensuring the cybersecurity of the group and its subsidiaries by performing security tests on its equipment and applications whether internal or external.
As part of these activities, vulnerabilities may be discovered. When such a vulnerability presents a significant risk, the Michelin CERT applies the vulnerability disclosure policy described in this document.
Michelin places great importance on protecting its customers, its digital assets, and those of its suppliers and that of the cybersecurity community. This policy defines a formal framework for ensuring that relevant vendors are notified, fixes are tracked, and transparency is maintained throughout the process.
The process detailed in this document reflects Michelin’s commitment to proactive and responsible cybersecurity, promoting collaboration with stakeholders while minimizing risks associated with identified vulnerabilities. However, this policy does not supersede existing contractual agreements with vendors. In the event of a conflict, the contractual terms take precedence ensuring mutual obligations are respected.
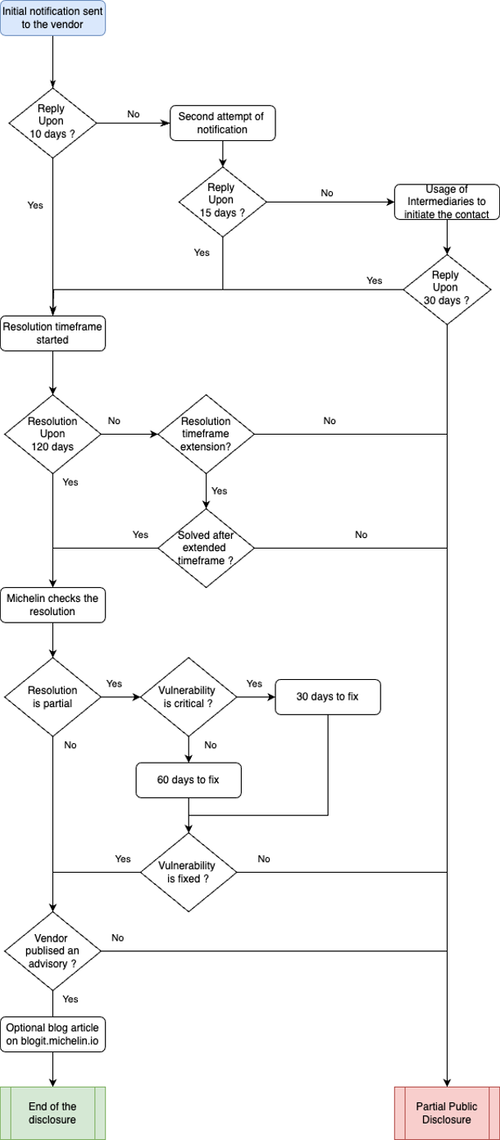
Initial notification to the vendor
When a vulnerability is identified:
The Michelin CERT will contact the relevant vendor through appropriate communication’s channels (such as contacts or formal mechanisms listed on the vendor’s website, emails to addresses such as “security@”, “support@”, “info@”, or secure@company.com to obtain further instructions).
Once contact is established and verified, a message including relevant details about the vulnerability—such as a technical description, potential impact, and steps to reproduce the issue—will be sent through a secure channel
At the same time, the Michelin CERT may inform its internal teams or deploy temporary measures to protect its own infrastructure and sensitive data, if necessary.
Follow-up and escalation
If the vendor does not respond to the initial notification within ten business days, the Michelin CERT will make a second formal attempt to contact them.
If there is no response after fifteen business days in total, the Michelin CERT may reach out to an intermediary (such as known contacts or specialized organizations) to establish communication with the vendor.
If after 30 business days all efforts to reach the vendor have failed, the Michelin CERT may consider a limited public disclosure to alert the community and reduce risks for its stakeholders.
Timeframe for resolution
Once contact is established, the Michelin CERT allows waits 120 days for the vendor to provide a public fix or mitigation.
If this target remediation period passes without an adequate response or reasonable explanation, the Michelin CERT reserves the right to publish a limited public advisory that includes information on available risk mitigation steps.
Extensions to this 120-day target may be granted at the discretion of the Michelin CERT, but only in exceptional cases justified by technical complexity or other significant constraints.
For vulnerabilities resulting from ineffective or incomplete patches:
For critical flaws with active or imminent exploitation, the vendor will have 30 days to provide a fix.
Other cases will have a 60-day resolution window.
transparency and collaboration
The Michelin CERT is committed to assisting vendors in understanding and resolving identified vulnerabilities. To that end, technical assistance may be offered to help analyze the issue, assess its impact, and identify appropriate remediation steps.
If a vendor decides not to fix a flaw, the Michelin CERT may consider collaborating on a public disclosure, accompanied by recommended workarounds.
To maintain transparency with the cybersecurity community, a summary of exchanges with the vendor may be published to provide insight into the efforts made to resolve the vulnerability.
Confidentiality commitment
The Michelin CERT commits to handling all reported vulnerabilities with the utmost discretion to protect the stakeholders involved. We do not disclose any specific technical details before a corrective solution is available, unless necessary to prevent an immediate risk to users.
As part of our responsible approach, all communications related to the vulnerability—including exchanges with the vendor—are carried out through secure channels to ensure confidentiality.
Additionally, Michelin ensures that access to vulnerability details is restricted to authorized personnel only, thus guaranteeing controlled and secure handling of sensitive information. This approach aims to prevent malicious exploitation and ensure responsible disclosure, in line with industry best practices and existing contractual obligations.
security advisory publications
All security advisories will be published in a dedicated section of the Michelin CERT website or via other official communication channels. These advisories will include technical information and recommendations to help protect users of the affected products or services.
This policy reflects Michelin’s ethical commitment to security and the protection of users of its products and services, all while encouraging responsible collaboration with external vendors and the cybersecurity community.